Quick guide to analysing a suspect’s financial affairs in a corruption case
How investigators and prosecutors can use Source and Application of Funds analysis to inform corruption and money laundering investigations and prosecutions and to generate evidence for use in court. A quick guide by the Training team of the International Centre for Asset Recovery (ICAR)at the Basel Institute on Governance.
If it looks and smells like corruption…
“How could he afford that car on his salary?” “Where did she get the money to buy those expensive clothes?” “How is that public official able to stay in a luxury beachside property when he only earns enough for a small house in the suburbs?”
These simple questions are often the starting point for investigations into suspected corruption, including under laws targeting unexplained wealth.
Answering them, and proving in court that the money has been obtained illicitly and should therefore be subject to recovery, is a lot trickier.
… that’s still not enough for a court
Corruption is a particularly difficult crime to investigate and prove beyond reasonable doubt. Why? Because it usually takes place behind closed doors between two or more willing parties who are unlikely to report the matter to the police or cooperate in an investigation.
These days, technologies such as digital transfers, mobile money and cryptocurrencies make it far easier for illicitly obtained money to change hands. Stolen funds disappear across borders and into secret accounts in a click. Many corrupt officials seeking to launder money also hire unscrupulous corporate service providers, accountants and lawyers. These professionals help them to create complex financial structures in offshore jurisdictions to conceal the true ownership of their assets, as explained in our quick guide to offshore structures and beneficial ownership.
These factors combine to thwart the attempts of investigators to follow the trail of the money.
Caught red-handed? Not often
The increasing sophistication of criminals means it is rare to find direct evidence of corruption or other financial crimes, such as an eyewitness, a video or audio recording, or a bank transfer from a company to a public official who can be proved to have performed a particular corrupt action in return.
Moreover, even such evidence is not conclusive. Witness accounts may be flawed, and documents, videos and audio recordings are nowadays easily forged.
This is why it is vital for anti-corruption officers to be able to build financial profiles of individuals suspected of corruption and money laundering. Systematically calculating the amount of money that a suspect has accumulated and spent during a particular period, compared to their legal and known income, is a powerful means to demonstrate, or provide corroborative evidence in respect of, their illicit activity even in the absence of a smoking gun.
Source and Application: a common-sense calculation
One particularly effective tool for building such a financial profile of a suspect is the Source and Application analysis.
It is a simple formula to calculate the difference between two figures over a specific period of time selected by the investigator and based on allegations or suspicions of corrupt activity:
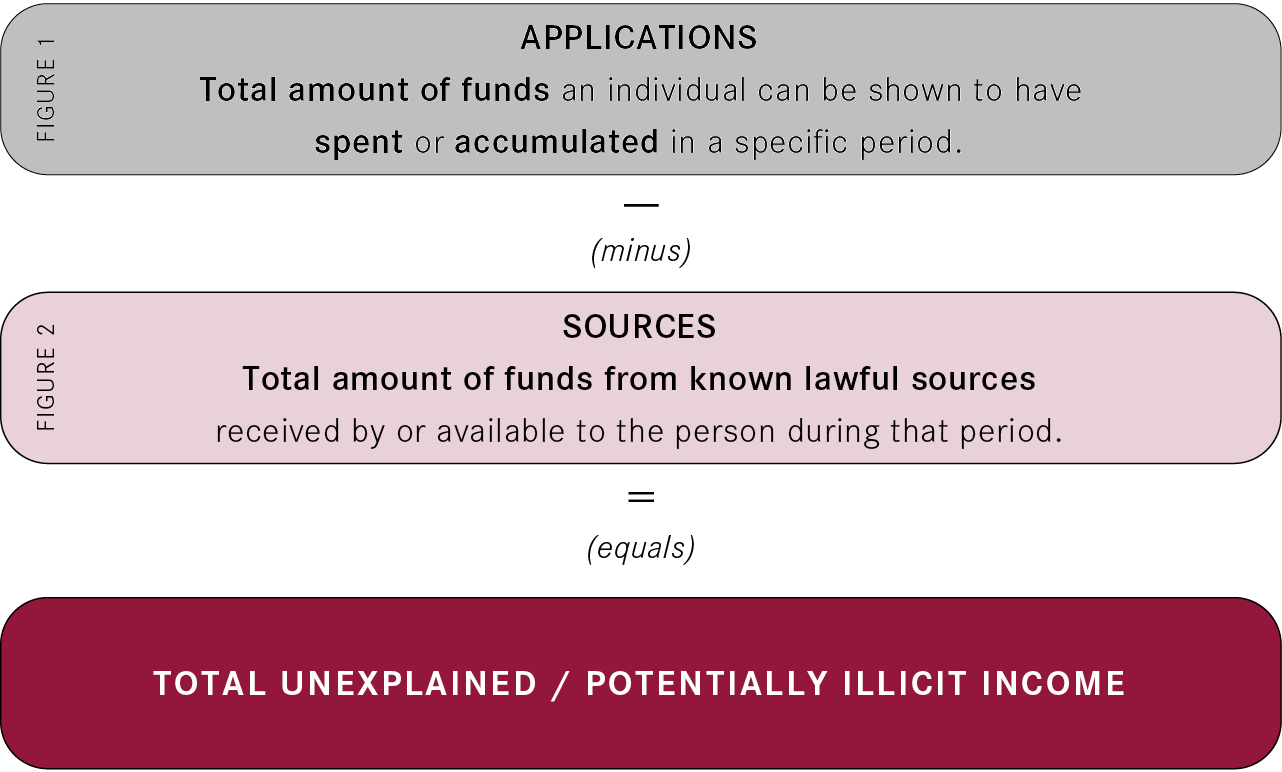
For example: If a suspect can be shown to have spent or accumulated $500,000 in 2020 but only had $250,000 legally available to her during this time according to official records and other relevant evidence, she has enjoyed $250,000 of unexplained income.
This amount may or may not be the proceeds of corruption, but unless she can explain the source of the additional money it is strong circumstantial evidence of illicit behaviour.
This financial evidence can be used in court to support a traditional corruption, fraud or money laundering case in a criminal context. In countries with illicit enrichment laws, it can also be used as direct evidence and as a basis for recovering the unexplained wealth. (For more on illicit enrichment, see our open-access book and its Annex II guidance on Source and Application of Funds analysis at illicitenrichment.baselgovernance.org.)
Gathering the information – a valuable exercise in itself
In addition to generating crucial financial evidence of illicit activity, the process of conducting a Source and Application analysis is a useful investigative tool.
This is because it offers a systematic framework for investigators to gather all documentary and other relevant evidence that relates to the suspect’s use of funds vs the funds legally available to him or her during a specific period of interest.
The Source and Application computation sheet in itself is not evidence per se but merely a method to organise and present financial evidence gathered during the investigation in a way that highlights or identifies illicit or unknown income.
Examples of legal sources of income are salary payments, declared income from property rentals or company shareholdings, sales of assets, inheritances or loans. This category also includes the suspect’s bank balances at the start of the period, since the money contained in these accounts was available for him or her to spend.
In terms of applications, investigators will use bank or mobile money statements, invoices and other documents to gather information about the suspect’s use of funds during that period.
This includes, for example, purchasing assets, paying property rentals or bills, repaying loans, employing staff or taking holidays. It also includes the suspect’s bank balances at the end of the selected period, as this reflects money he had not yet spent but still had available to spend. Other applications may involve the purchase of crypto assets which can be kept in a self-custody wallet or with a third party such as a cryptocurrency exchange.
All of these documents and other relevant evidence can contain vital clues that assist in tracing illicit flows of money and reveal further suspects in the individual’s corrupt network.
No silver bullet, but a useful tool
There are challenges to using the Source and Application analysis, of course.
One arises in countries with large informal and cash-based economies, which makes it harder to obtain documents and records to prove either the source or the application of a suspect’s funds.
Good old-fashioned detective work can help to overcome this, such as surveillance, speaking to neighbours and knowing the market prices of goods that a person claims to have sold. Furthermore, this tool is not meant to be used in each and every corruption case but rather when it appears that the suspect is enjoying a lifestyle that is not commensurate with his/her legal and known income.
Another difficulty is finding hidden assets, bank accounts, mobile money accounts or cryptocurrency wallets, especially when the suspect refuses to cooperate or the information is held abroad or protected by banking secrecy laws. Our quick guide to fundamental skills in tracing assets gives investigators some tips on uncovering new leads, again through good old-fashioned detective work. Meanwhile our guide to international cooperation explains how investigators may obtain such information from foreign jurisdictions, and our quick guide to cryptocurrencies and money laundering reveals how it is possible for law enforcement to “follow the virtual money”.
In court, it may be that magistrates and judges are unaware of this method or unwilling to accept the final computation as financial evidence. We do believe, though, that it is much simpler to explain a Source and Application calculation than alternative methods of financial profiling such as Net Worth analysis, as explored in our free eLearning course on Source and Application of Funds analysis.
There is no silver bullet or magic tool to calculate illicit funds in a corruption case and generate rock solid financial evidence of wrongdoing. But the analysis is often a crucial piece in a complex puzzle that can prove, or corroborate evidence of, the possession of illicit assets and point to related criminal activity.
In our experience conducting training programmes around the world, we see time and again how the Source and Application analysis resonates with investigators and prosecutors as both a useful tool in investigating corruption and money laundering cases and generating evidence of these crimes for use in court.
